Learn How To Secure Business Data With Endpoint Protector USB Enforced Encryption
In this article, we will learn how to secure your business data with Endpoint Protector USB Enforced Encryption.
USB (Universal Serial Bus) storage devices are portable, popular, and convenient. It stores the data and allows us to transfer data between computers. Simply plug it into a USB port, copy the required data and remove the USB from the port. The major disadvantage of USB storage devices is the threats it brings to your data due to the security weakness in the form of encryption.
Data can be easily lost when it is in transit. Data thefts and Data leakage are quite common now adays.
BYOD Policy: Many companies have a ‘Bring Your Own Device’ (BYOD) policy at work where employees bring in their USB devices and connect them to company computers.
COVID-19: The World Health Organization declared the COVID-19 a pandemic. COVID-19 had a significant impact on the way everyone lived and worked. Companies around the world have encouraged their employees to work from home to protect their health and stop spreading the virus.
When we are working from home, we use devices outside of our computer networks.
Sometimes even simple errors tend to huge data loss.
Encryption of USB devices is important in boosting the security process of transferring data. The right level of Encryption can be the difference between a secure file and leaked data.
What is USB Encryption?
Simply put, USB encryption is a form of data encryption that allows you to secure your personal data with the aid of a password or encryption key. All personal information, as well as computer code that is stored on a USB drive, cannot be read by anyone else without the proper key. That is why you should get the right software for the job.
Why is USB Encryption needed?
Simple, hackers have become quite clever. They know how to get into your computer in a matter of minutes, and they also know how to manipulate the information that gets stored. The result is that they can easily access all of your personal data and take advantage of all of the things that you did not mean to disclose.
So, if you are worried about identity theft or about people gaining access to your information because you accidentally deleted files, then you should look into USB encryption.
The fact is that your data is very important. So, make sure that you take the time to learn more about USB encryption and how it can help secure your data.
Keep in mind that your information is precious. So never do a mistake by leaving it vulnerable.
Businesses should also be aware that there are a number of different ways that your data can become vulnerable to unscrupulous individuals. Some of these include Trojans, worms, malware, and even more sophisticated forms of intrusions.
To keep your information safe from prying eyes, you should consider using Enforced Encryption by Endpoint Protector.
It’s an easy way to ensure that your private data is kept safe and secure on your computer.
What is USB Enforced Encryption?
Encryption scrambles data in transit to an unreadable human format, which prevents unauthorized access to the information on USB devices. Only authorized users (i.e., the one with the encryption key) can access the data on these devices.
Securing your business data through Encryption is essential from a security and compliance point of view.
Enforced Encryption is one of the modules by Endpoint Protector, which is used for automatic USB encryption. It keeps your data secure, not only on hard drives but also on removable devices, like USB.
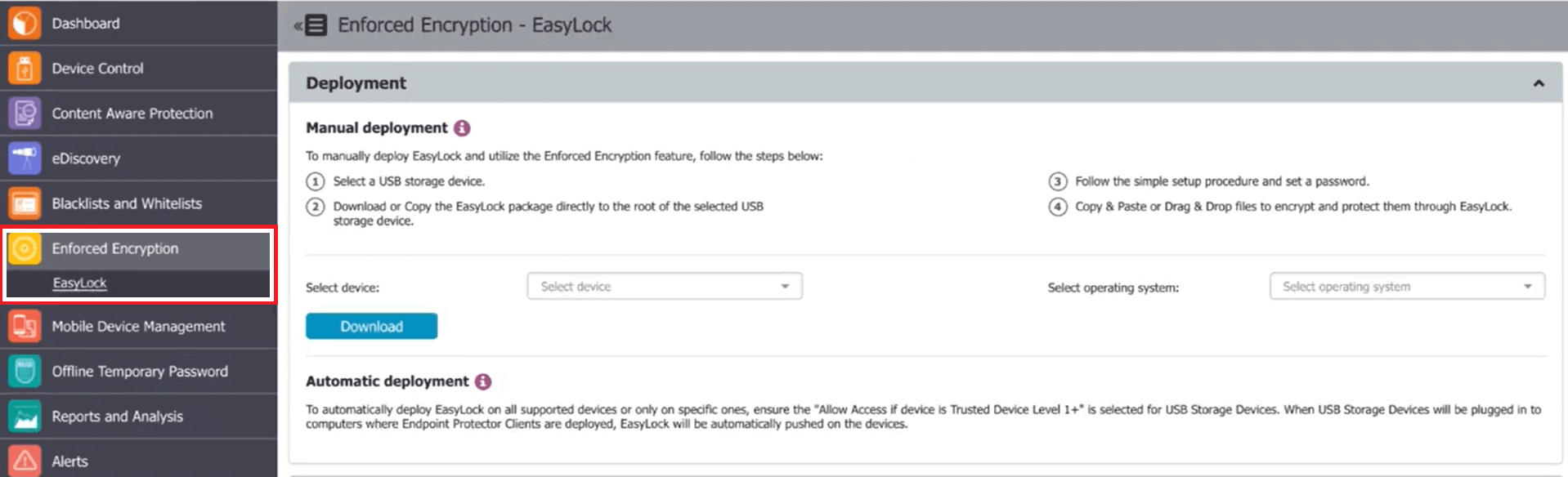
This is a software tool that is designed to encrypt your data before sending it over a USB cord or to another computer. When you are using Enforced Encryption, it ensures that your data is safe even if multiple devices can potentially access your data.
Features of Enforced Encryption
Faced with increasingly more restrictive data security regulations and also the danger of cyberattacks, businesses large and small have recently made information security a high priority. However, as they invest in complex strategies to shield data within their company networks, they often overlook one of the greatest sources of data flows: data in transit.
Most data files that people store on their drives are often sensitive. That’s why it’s very important to secure the information you’re carrying or sending. In addition, if your data is easily readable, hackers could also access this very easily. This is where encryption comes into play.
In the modern business world, workers often travel for work, regularly attend meetings where they are predicted to hold presentations and seminars where they exhibit their products to attract new clients. These situations imply devices on the move, in a hectic, overcrowded surrounding, very much beyond the security of a company network. A moment’s diversion is all that stands between an organization and information loss.
Endpoint Protector’s Enforced Encryption ensures that any company data copied onto USB devices will be automatically encrypted with US government approved 256bit AES CBC-mode encryption.
Here are some features of Enforced Encryption:
#1. Cross-platform capacities
- It is rare nowadays for companies to use only one OS across the company. Whether it is executives, designers, or marketing professionals using Macs or Windows, businesses need cross-platform solutions. That is why companies need to search for cross-platform solutions when protecting data on the move.
- Not only that, it offers various features for both operating systems. Admins may also control its installation and preferences from the exact same dashboard, irrespective of the OS they themselves are using.
#2. Automatic and manual deployment
- Endpoint Protector offers an easy-to-use and intuitive interface.
- Admins can automatically deploy EasyLock from Endpoint protector dashboard.
- With a simple drag and drop interface, files can then be easily copied to and from the EasyLock client installed on the root of the device.
- Users and admins can also perform a manual installation. They can download the EasyLock customer, copy it on a USB device, and execute it from the root.
- Due to its extensive security features, these manual installation files can only be used once. A new file has to be downloaded for every setup.
#3. Complex passwords
- Admins can enforce strong password rules to ensure data on USB devices stays secure once it is encrypted.
- Password length, a minimum number of uppercase, lowercase, special characters & numbers, allowable limit for incorrect passwords, and so on can be controlled by Admin.
- Complex password settings allow admins to specify the mandatory length of passwords and the standards of their makeup.
- They could pick the minimum amount of upper and lowercase letters, special characters, and numbers. They can also set a validity period to get a password and how many tries someone must enter it correctly.
#4. Resetting passwords and devices remotely
- Admins can remotely control USB devices having EasyLock installed. Through them, they could send messages to users and reset passwords if they have been compromised or forgotten.
- USBs may also be filtered remotely by resetting the device, effectively deleting the EasyLock client and all the encrypted files.
#5. File tracing
- EasyLock also comes with a File Tracing alternative. Once turned on, this attribute records and logs all information transferred to and from devices using EasyLock.
- The logs will then be sent into the Endpoint Protector Server when the unit is connected to a computer using an Endpoint Protector Client installed.
- It also works on Offline mode. EasyLock can store the logs locally in an encrypted format on the apparatus until it is linked to a computer with an Endpoint Protect Client present.
How USB Enforced Encryption Works?
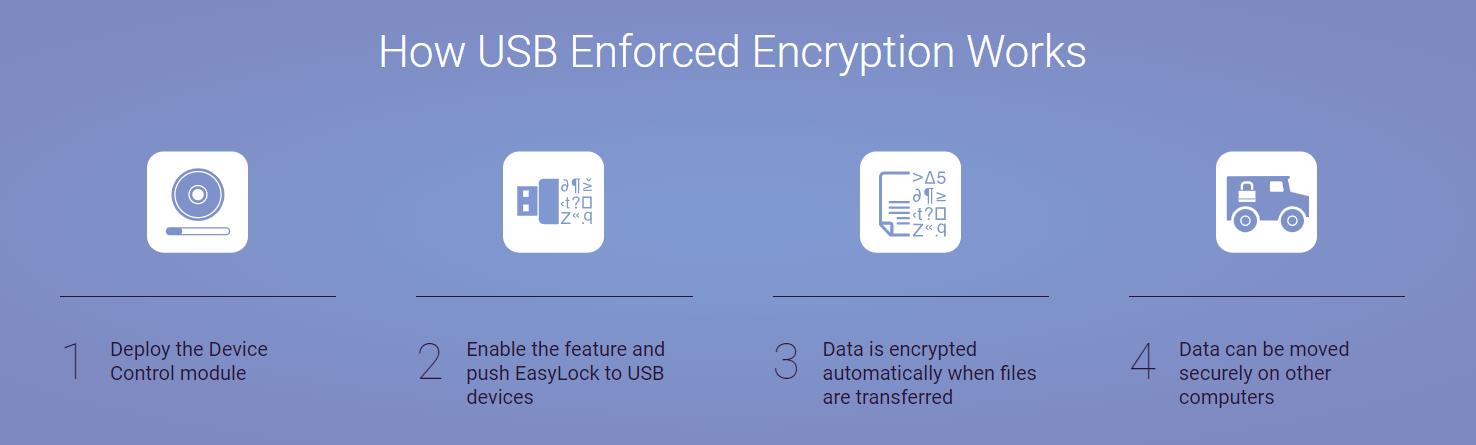
- Deploy the Device Control module in Endpoint Protector.
- Enable the feature and push EasyLock to USB devices.
- Data is encrypted automatically when files are transferred to another device.
- Data can be moved securely on other computers.
Concept of TrustedDevice
TrustedDevice is an innovative technology in the endpoint protection environment. It is designed to link endpoints’ data loss prevention with encryption at the device level to increase the strength of data security.
It deals with the unintentional employee mistake resulting in the data breach. Every day, stories about lost notebooks or mobile storage devices exposing healthcare records, social security numbers, financial, billing, or account details of millions of people are seen in the news.
TrustedDevices technology is incorporated with Endpoint Protector, Data Loss Prevention solutions and, EasyLock to achieve far better device control and policy enforcement for data at endpoints. It is going to easily ensure support for sensitive information dissemination inside and outside the company network.
TrustedDevices – 4 Security Levels
Level 1
It provides security for small businesses and enterprises with a focus on software-based encryption for data security. Any USB Flash Drive can be turned into a TrustedDevice Level 1 with EasyLock.
Level 2
It offers a medium-security level with biometric data protection or advanced software-based data encryption and also includes FileVault encrypted devices.
Level 3
It offers a high-security level with strong hardware-based encryption mandatory for sensitive enterprise data protection as regulatory compliance like SOX, HIPAA, GLBA, PIPED, DPA, or PCI 95/46/EC.
Level 4
It provides maximum security for military, government, and even secret agencies use. It uses strong hardware-based encryption for data protection.
A typical scenario would imply deploying the Endpoint Protector Client on an endpoint. To avoid data loss or data theft, device rights will probably likely be configured to block almost any USB storage device.
If EasyLock is currently on a specific device, access to it would be enabled as any copied files will be encrypted and secured. The TrustedDevice Level 1 implies the EasyLock application has to be preinstalled on a USB storage device in order to be permitted via Endpoint Protector.
The TrustedDevice Level 1+ suggests that EasyLock Enforced Encryption is also activated and accredited through Endpoint Protector. In this situation, EasyLock can be deployed automatically on almost any USB storage device that connects to the secure endpoint (if not specified).
If TrustedDevice fails to get authorization from Endpoint Protector, it will not be usable by anyone. The device will be blocked, and the user will not be able to access the device.
EasyLock With Endpoint Protector
Protecting data in movement is necessary to ensure no third party has access to confidential information. Regardless of where the data is stored – saved on USB devices, CDs, DVDs, local folders, cloud storage solutions – encryption can be the best solution in case a device is lost, misplaced, or stolen.
EasyLock by Endpoint Protector is a cross-platform, enterprise-grade data encryption service designed to keep confidential business data safe.
It is suitable for any user type, from novice to expert, from home users to multinational employees.
EasyLock Enforced Encryption is a stand-alone application, which protects data on USB storage devices with government-approved 256bit AES CBC-mode encryption.
This is also available for local folders, CDs & DVDs, and cloud storage solutions.
This software also allows USB storage devices to be identified in TrustedDevices 1+.
This module can only be used in combination with Endpoint Protector. It provides enforced encryption options for any USB storage device that connects to the protected computer and remote management of those devices (resetting passwords, sending messages, resetting devices, etc.)
It offers an intuitive Drag & Drop interface. With this feature, files can be quickly copied to and from the device for fast, secure, and efficient workflow.
Pricing
Request pricing for Endpoint Protector. You can also get a free demo on request.
Benefits of Endpoint Protector’s USB Enforced Encryption
#1. An extra layer of security
Utilizing Enforced Encryption, users can transfer confidential data only on encoded USB portable storage devices. Data will be secure even when a device is lost or stolen, on account of the password-protected encrypted place.
#2. Regulatory Compliance
Many industry regulations want confidential data to be encrypted regardless of where it resides. Enforced Encryption assists compliance with HIPAA, PCI DSS, SOX, and many others, securing USB devices.
#3. Data Leakage Prevention
The Endpoint Protector will be enhanced when combined with functionalities of EasyLock Enforced Encryption, making sure sensitive data is secured, and information leakages are averted.
#4. Automatic deployment with TrustedDevice Level 1+
If selected in the Endpoint Protector Device Control software, this policy automatically deploys EasyLock on any USB device connected to computers that have the Endpoint Protector installed, simplifying the IT Administrator’s work.
#5. Business continuity
Reduce risks of data losses that can influence business due to fines, lawsuits, and negative brand image. Take care of your enterprise instead of managing data loss consequences.
Conclusion
Failing to implement company-wide encryption can lead to a huge financial and data loss in business.
EasyLock USB Enforced Encryption brings together convenience and ease of use into one convenient package. You will be able to secure your confidential data with the simple push of a button from anywhere you like. The best thing about this software is that it offers complete protection against USB security breaches, protecting your privacy, confidential information, and private data.
Related posts:
- Best Data Loss Prevention Software
- Best Device Control Software
- Best Digital Guardian DLP
- Best Forcepoint DLP Alternatives
- Best Mcafee DLP Alternatives
- Best Symantec DLP Alternatives






